How AI can help your DevSecOps pipeline
There’s a dirty little secret that every programmer knows. We’re awful at securing our code. To try to deal with this, rather than wait for enraged customers to start screaming at the tech-support crew over the latest Common Vulnerability Scoring System (CVSS) 10 score from hell, Shannon Lietz, then Adobe’s VP of Vulnerability Labs, coined the concept of DevSecOps.
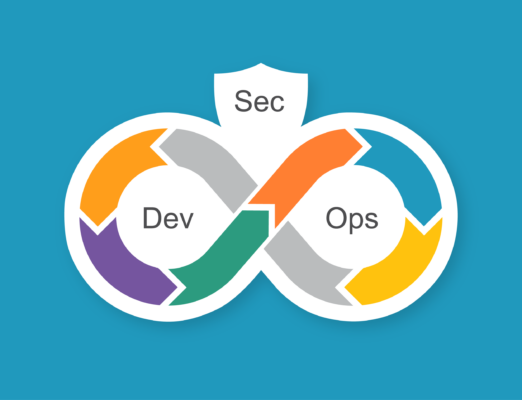
Like the name says, this approach incorporates security into the entire development lifecycle via DevOps. DevSecOps isn’t an after-the-fact add-on. It’s a software development approach that integrates security practices and automation into every phase of the development pipeline from the very start to the end by making security a shared responsibility of development, security, and operations teams.
DevSecOps (sometimes called “DevOpsSec”) builds on the principles of DevOps by embedding security “from the start,” not as a final checkpoint. Specifically, this means security is considered during initial planning, coding, integration, testing, deployment, and ongoing operations. Automation is used to continuously scan for vulnerabilities, enforce compliance, and monitor risk, enabling fast and secure software delivery. This process of baking security from day one is called “shifting left.”
Its key features are (drum roll, please):
- Collaboration: Developers, security teams, and operations work together, sharing responsibility for security.
- Automation: Security testing, static code analysis, and compliance checks are automated throughout Continuous Integration and Continuous Deployment (CI/CD) pipelines.
- Continuous security: Monitoring, alerting, and threat detection run in real-time, making it possible to identify and resolve issues earlier and reduce risk.
Numerous companies and government agencies, such as Wipro, Telefónica UK, and the US Department of Defense (DoD), rely on DevSecOps for cloud, application, and infrastructure security. They’re largely using it to modernize and secure legacy systems and automate deployments.
What they’re doing with it is automating CI/CD security checks; examples include integrating static code analysis, container scanning, and API tests directly into their pipelines, stopping vulnerabilities before code reaches production. Organizations build continuous risk and threat assessments into their pipelines so teams can respond in real time to new exploits and system anomalies. Others are deploying it to the increasingly critical issue of securing their software supply chain defense against chain attacks.
You should use AI to reduce your manual overhead, not to replace it.
Many organizations, especially businesses that deploy a lot on Amazon Web Services (AWS), Azure, and Google Cloud, are using it to secure their use of infrastructure-as-code tools such as OpenTofu, Spacelift, Terraform, and Ansible with embedded security modules, lowering cloud breach risks.
Finally, it’s also common to use DevSecOps to manage companies’ compliance requirements for GDPR, PCI DSS, and all the other laundry list regulatory requirements.
It all sounds good, doesn’t it? However, there are several big flies in the DevSecOps soup. As a Progress Software study pointed out in 2023, we’re really bad at implementing DevSecOps.
Specifically, users didn’t really understand the DevSecOps technique, such as prioritizing security efforts, securing different types of workloads, and meeting delivery deadlines and audit requirements. This means–you can see this coming, can’t you?– that they have a devil of a time getting management on board or showing a return on investment (ROI) to the bean counters.
It seems that no matter how we try, we suck at securing our code. What’s a poor development team lead to do? Look to AI for help, of course.
DevSecOps and AI
I tend to be an AI cynic, but I think AI may be able to help here. Considering our sad security track record, it certainly can’t hurt.
Well, actually, it can. Just ask Daniel Stenberg, chief maintainer of the popular open-source cURL data transfer program. As far as he’s concerned, AI-written bug reports are active attacks on the project. Certainly, using AI to hunt for problems without thought can just create more busy work.
That said, used with care by someone who knows what they’re doing, AI can be a help. As Sasha Levin, Linux kernel hacker and Nvidia distinguished engineer, observed after using AI to make a Linux kernel patch, “This is a great example of what LLMs are doing right now. You give it a small, well-defined task, and it goes and does it. And you notice that this patch isn’t, ‘Hey, LLM, go write me a driver for my new hardware.’ Instead, it’s very specific — convert this specific hash to use our standard API.”
Particularly for AI and DevSecOps, companies are turning to AI to automate tedious processes such as vulnerability scanning, code analysis, and compliance checks. Machine learning (ML) systems can analyze data and system behavior in real time, identifying anomalies and potential threats before they reach production. This enables you to spot security issues and resolve them earlier in the software development lifecycle..
People are also using AI-supported vulnerability scanners such as Darktrace PREVENT, Qualys VMDR, and Microsoft Defender Threat Intelligence to scan code and dependencies, detect issues, prioritize risks, and suggest fixes automatically. Let me emphasize the word “suggest,” simply taking these suggestions as Gospel is just asking for trouble.
The same is true of AI’s patch management and compliance auditing suggestions. You should use AI to reduce your manual overhead, not to replace it. If you don’t, you’ll only replace human error with AI error. Today, several patch management tools are leveraging AI for automated vulnerability detection, prioritization, and smart patch deployment. Some of the best include: CrowdStrike Falcon, Tanium, and NinjaOne.
The benefits of all this are to introduce streamlined AI-driven automated regression testing, static code analysis, and pipeline monitoring. This, in turn, should make your releases faster and less error-prone.
You can also use ML to be more proactive in detecting threats before they bite you in the tuchus. They can do this by integrating security notifications, security logs, and system metrics to spot possible compromises and respond to incidents before they escalate. Programs that help with this are: Microsoft Security Copilot, Vectra AI, SentinelOne, Radiant Security, and HiddenLayer.
When it all works together well, we should see our entire development cycle run with less noise and increased clarity: By aggregating data from across the toolchain, AI provides actionable insights, allowing Dev, Sec, and Ops teams to work more smoothly together.
Note, I said “should.” It’s tempting as it is to let AI do it all once it’s integrated into your pipeline. Don’t do it. AI blunders all the time. The very best AI programs are often blind to edge cases. AI chatbots also have a truly annoying habit of assuring you that yes, they know exactly what they’re doing, when they’re talking complete rot.
Treat AI as a very fast, but not particularly bright or experienced intern. With this approach, you should see speed and quality gains in your pipeline. It won’t be as fast as you might like it to be, but you and your programs will be much safer.